

Open Networking is not a new concept. SONiC (the Software for Open Networking) has been around for some time, and cloud-managed campus switches based on proprietary NOS (Network Operating System), are also not new. What’s truly novel is the comprehensive solution that finally brings open-source SONiC to the campus networks and adds to it a layer of cloud management and zero trust provisioning, all running on a cost-optimized hardware platform specifically tailored to campus networks: “Cloud Managed Enterprise” or CME.
In recent years, Open Networking offered the hyperscale operators the option to use open-source software on a variety of merchant silicon, providing freedom from the lockdown imposed by the big system vendors. The next challenge was to bring similar benefits to campus networks, particularly to what is now referred to as CME.
This blog will demonstrate how the Marvell ® Prestera® switches, equipped with a comprehensive Software Development Kit, along with the collaborative efforts of a vibrant industry community called OpenLAN Switching (OLS), have created this open cloud-managed solution for campus networks.
The power of a community
The first thing to recognize is that it took teamwork from multiple companies to create this open solution. Under the umbrella of the Telecom Infra Project (TIP), various companies gathered and created a working group called OpenLAN. Within OpenLAN, two sub working groups formed: OpenWi-Fi and OpenLAN Switching (OLS), which is the subgroup relevant to this discussion.
Numerous companies actively participated in the collaborative effort—Figure 1 mentions just some of them—organized according to their role in the solution.
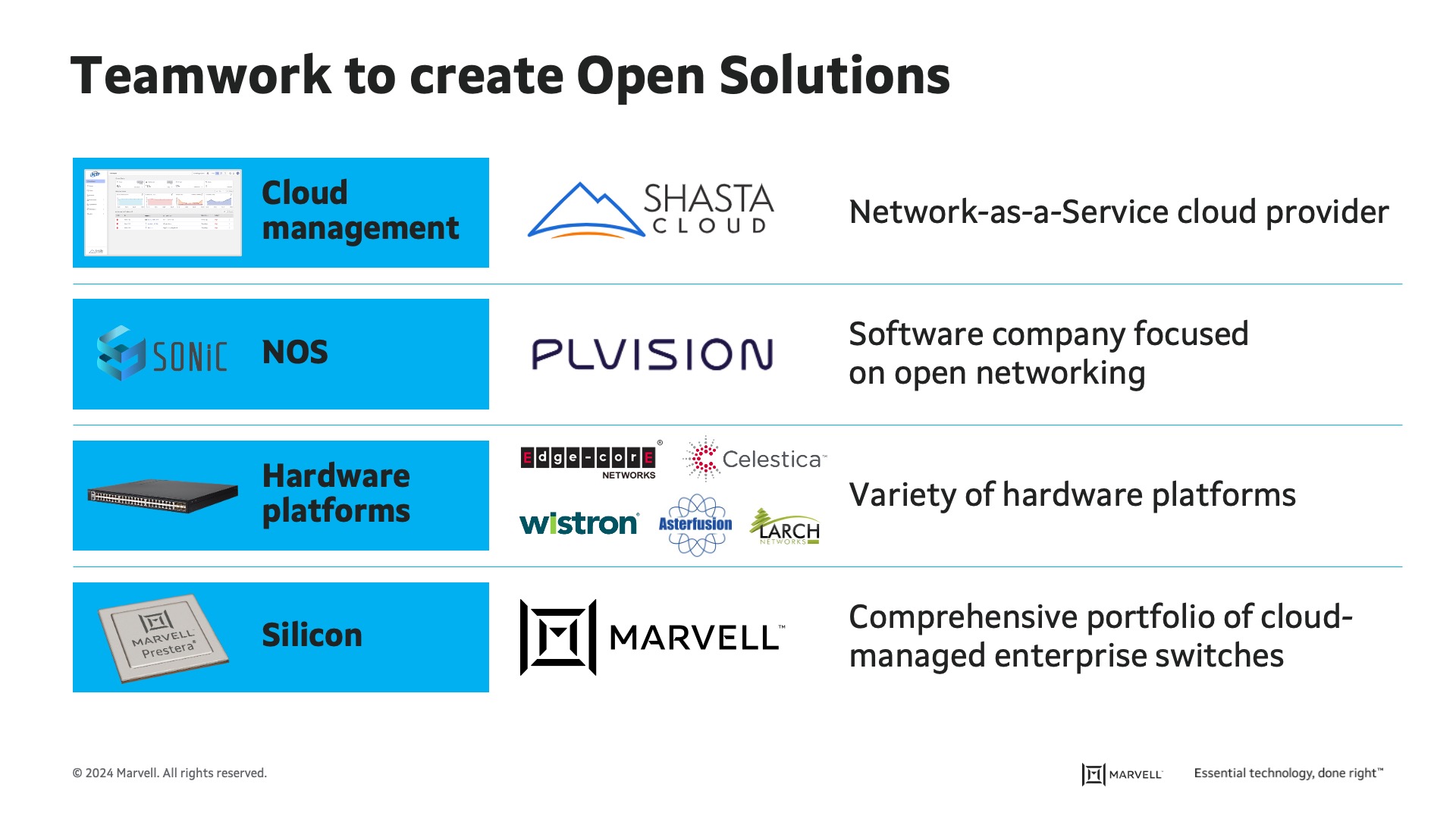
Figure 1: Breakdown of companies involved in OpenLAN Switching
At the center of this solution lie the semiconductor companies providing switch silicon, along with Marvell providing the Prestera® Switch family, for the cloud managed enterprise (CME) market.
Then there are a variety of hardware (HW) platforms from different vendors. It is the first time that there are so many companies committed to running open software on the Marvell-based platforms.
On top of that, there is the Network Operating System (NOS). While the OLS community doesn’t mandate its use, many companies have embraced SONiC, which proved itself in the data center and is now making its way into campus networks. This didn’t come without challenges, and companies like PLVision are actively making the necessary adjustments to SONiC to adapt it to this market. It is worth noting that SONiC does not always take the form of open source. Some companies have chosen to create their own SONiC distribution, providing another level of support, validation and even additional features, but at the expense of not being open source.
The OLS community introduced a unique element specifically tailored for campus networks: the cloud management solution. Instead of using Network Management Systems (NMS) provided by the system vendor—which typically works only with the proprietary NOS provided with the switch, companies are now specializing in cloud management solutions that manage devices running open-source SONiC via the open interface that was created. One such company is Shasta Cloud, which is a Network-as-a-Service company and one of the driving forces behind the OpenLAN Switching activity, but there are others like NetExperience and Indio Networks that provide similar cloud management applications using the same open interface. Such cloud management solutions enable a new type of enterprise: the Cloud Managed Enterprise (CME). These enterprises harness the power of the cloud to centralize and simplify network management in a cost-effective and secure manner.
The OpenLAN Switching (OLS) group
The OpenLAN Switching (OLS) sub-group was built on the foundation of the OpenWi-Fi group, which was providing open Wi-Fi Access Points. It became clear that these Access Points needed to be aggregated by Ethernet switches, and the open solution needed to be extended to support such switches.
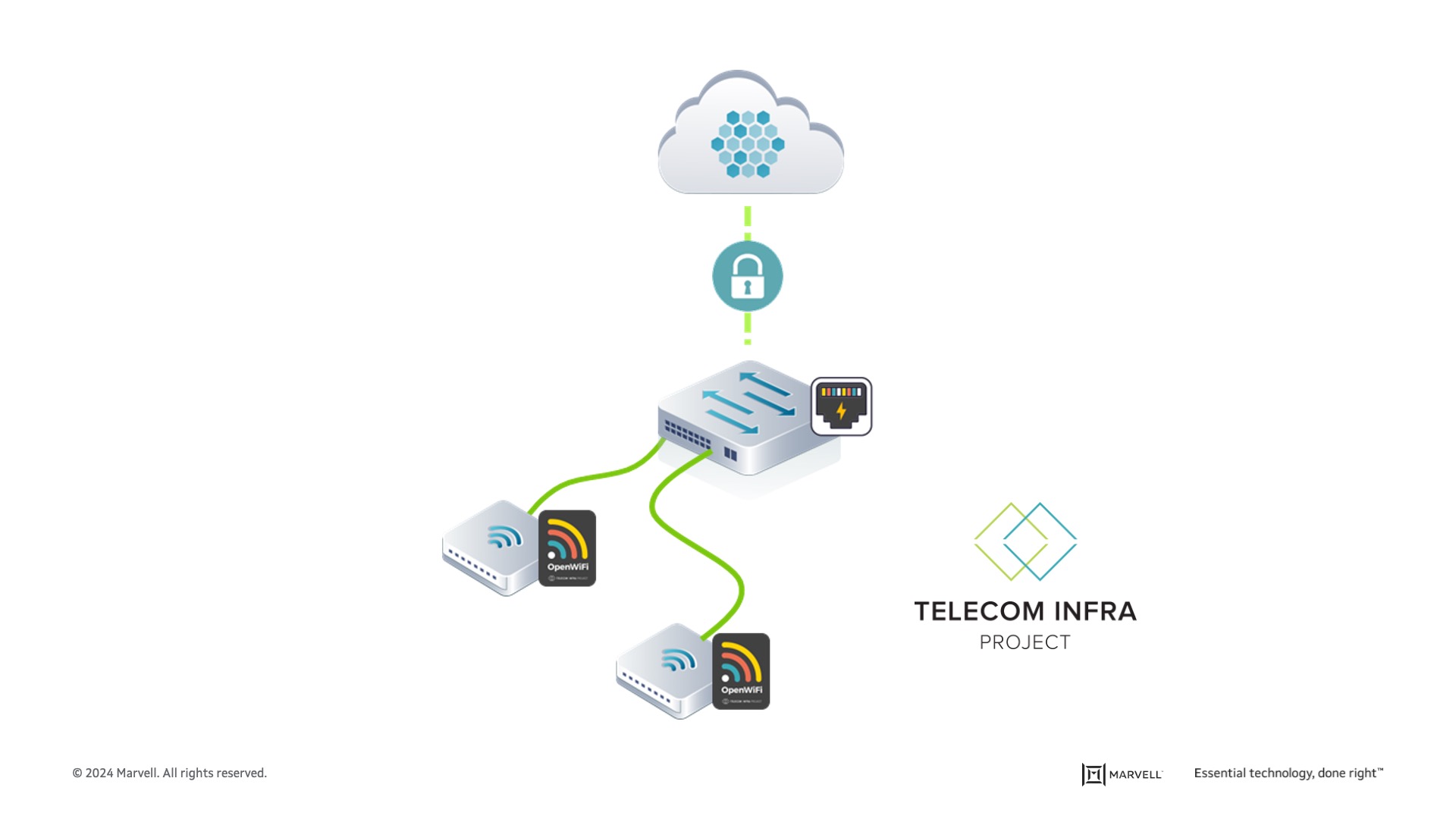
Figure 2: OpenLAN Switch (OLS)
The OLS community recognized that to support the variety of campus networks it needed switches that span from 8 ports to 48 ports to connect to the Access Points, not only via 1GbE links but also via 2.5G to 10Gbps copper port, to accommodate the newer Wi-Fi 6E and Wi-Fi 7 Access Points. Additionally, the switches had to provide Power over Ethernet (PoE) and PoE++ capabilities to power up those strong Wi-Fi Access Points.
The OLS team’s objectives extended beyond open-source solutions and defined an open interface toward the cloud, creating a secure connection and incorporating zero-trust provisions over the public internet. Furthermore, the entire OpenLAN group strives to deliver a validated and hardened solution. Recognizing that enterprise users cannot be expected to independently test and validate the solution themselves, the TIP organization plays a crucial role in validating and creating a “ready-to-use” out-of-the-box solution.
Comparing campus and cloud data center networks
When analyzing campus and branch office networks in comparison to cloud data centers where SONiC was already deployed, several key differences became evident.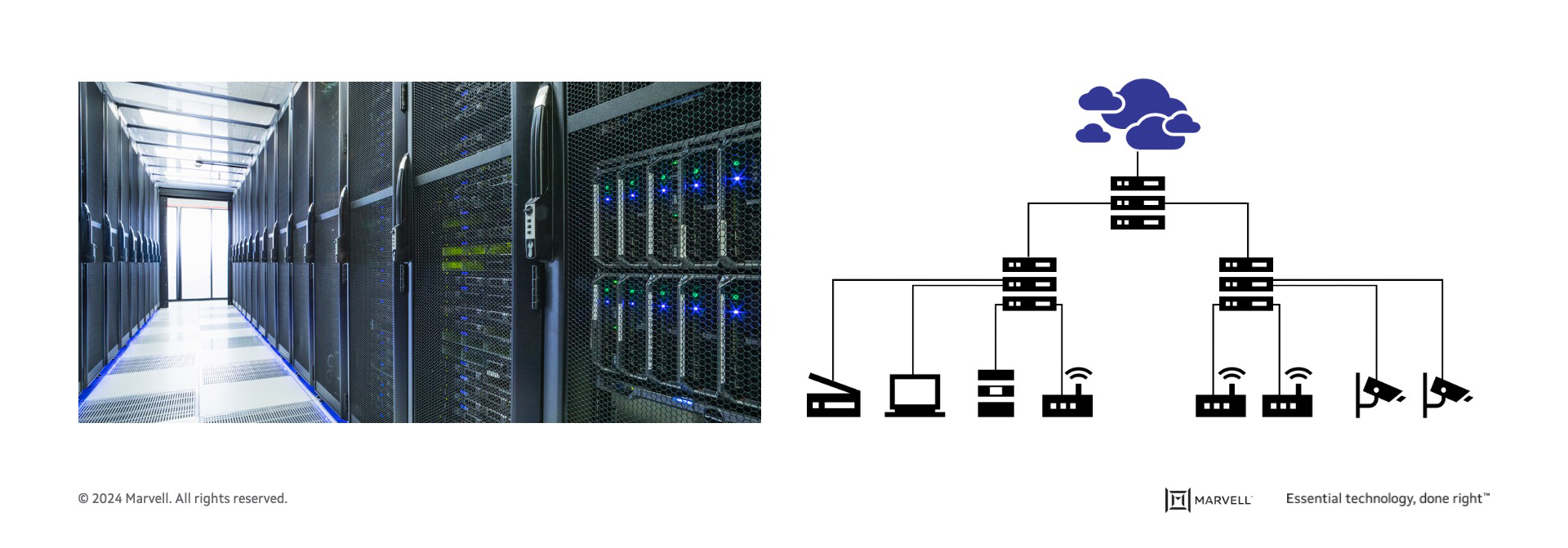
Figure 3: Campus vs. cloud data center
The hyperscale data center networks exhibit a well-organized, repetitive topology. They operate within a trusted and tightly controlled environment, managed by highly skilled and trained personnel that often have dedicated teams to build their own orchestration solutions. This contrasts with campus networks which can be an automated warehouse that doesn’t have any on-premises personnel or a small office with no dedicated IT team. The variation of topologies in campus networks is endless: they can be a grocery store with a variety of IOT devices including surveillance cameras and many sensors or a small office with a few access points and a printer. Basically, almost every network is different.
This led to the new CME trend of managing the network from the cloud over an unsecure public network without having a management station on the premises. Installation processes also differ. In campus networks, the goal is to be able to send a box via a courier, have a non-technical person be able to open the box, place it in position, plug it in and ensure that it works on the first time.
When analyzing the switch hardware and its bill of material, it was learned that, instead of powerful x86 CPUs designed for other applications, the CPUs available for running the Network Operating System—SONiC, in the case of Marvell—are modest ARM processors with limited RAM and flash storage.
On the other hand, each switch has limited scale and functionality, which allowed for trimming down SONiC and creating a lighter SONiC version which is still open source but can fit the CPU embedded inside the cost optimized switches being offered for this market.
The OLS technical solution
The OpenLAN Switching (OLS) group has defined and realized all the components necessary for a self-driving network, as can be seen in Figure 4 below.
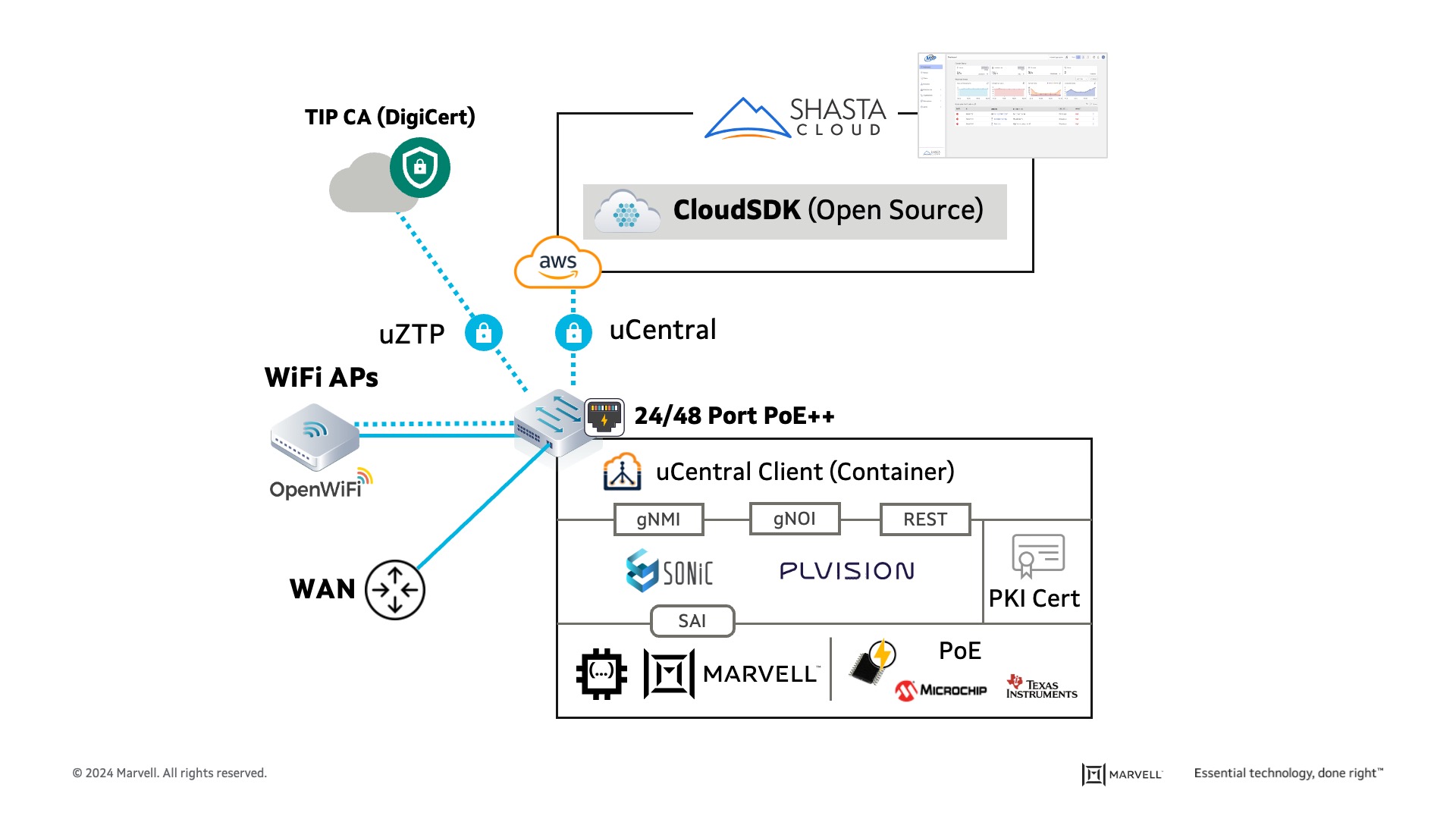
Figure 4: The OLS technical stack
The solution is centered around a PoE enabled Ethernet switch, which aggregates Wi-Fi Access points, IOT devices and other wired devices.
This switch is built around the Marvell Prestera silicon or offerings from other providers, that comes with a full Switch Abstraction Interface (SAI), or SDK as defined by the Open Compute Project (OCP) community.
Given that the switch also incorporates PoE components requiring management, Marvell recently contributed a PoE management solution to the OCP SAI community, and it is now part of the latest SAI release.
On top of SAI, there is the Network Operating System (NOS). The OLS community made a deliberate choice to standardize the interface between the node and the cloud, avoiding the imposition of a single NOS type. However, many individuals in the OLS community have chosen to focus on SONiC as their NOS and to adapt it for the OLS use cases. This adaptation involved three elements:
For cloud management, the OLS provided Cloud SDK, an open-source package that forms the infrastructure for the entire cloud management application. Companies like Shasta-Cloud build on top of the Cloud SDK graphic user interface, which shows the configuration and automation of the network. In collaborating with large system integrators, these companies offer a full service to the end customer, eliminating the need for dedicated IT departments.
Zero Trust Provisioning (ZTP)
Another key aspect in the solution is the Zero-Trust Provisioning (ZTP), a fully automated process that is described in Figure 5 below. When the switch is unboxed and installed at its destination within a business site, it already comes equipped with a PKI certificate from the original design manufacturer (ODM). The authentication process involves the switch connecting to a TIP Certificate Authority (CA) server, which then instructs the switch to which cloud management provider it should connect. Once a secure channel is established with the correct cloud provider, the switch can receive an updated software image and the appropriate configuration based on its network location. With these steps completed, the switch is ready to handle packet switching, event transmission, and periodic, secure telemetry streaming to the cloud.
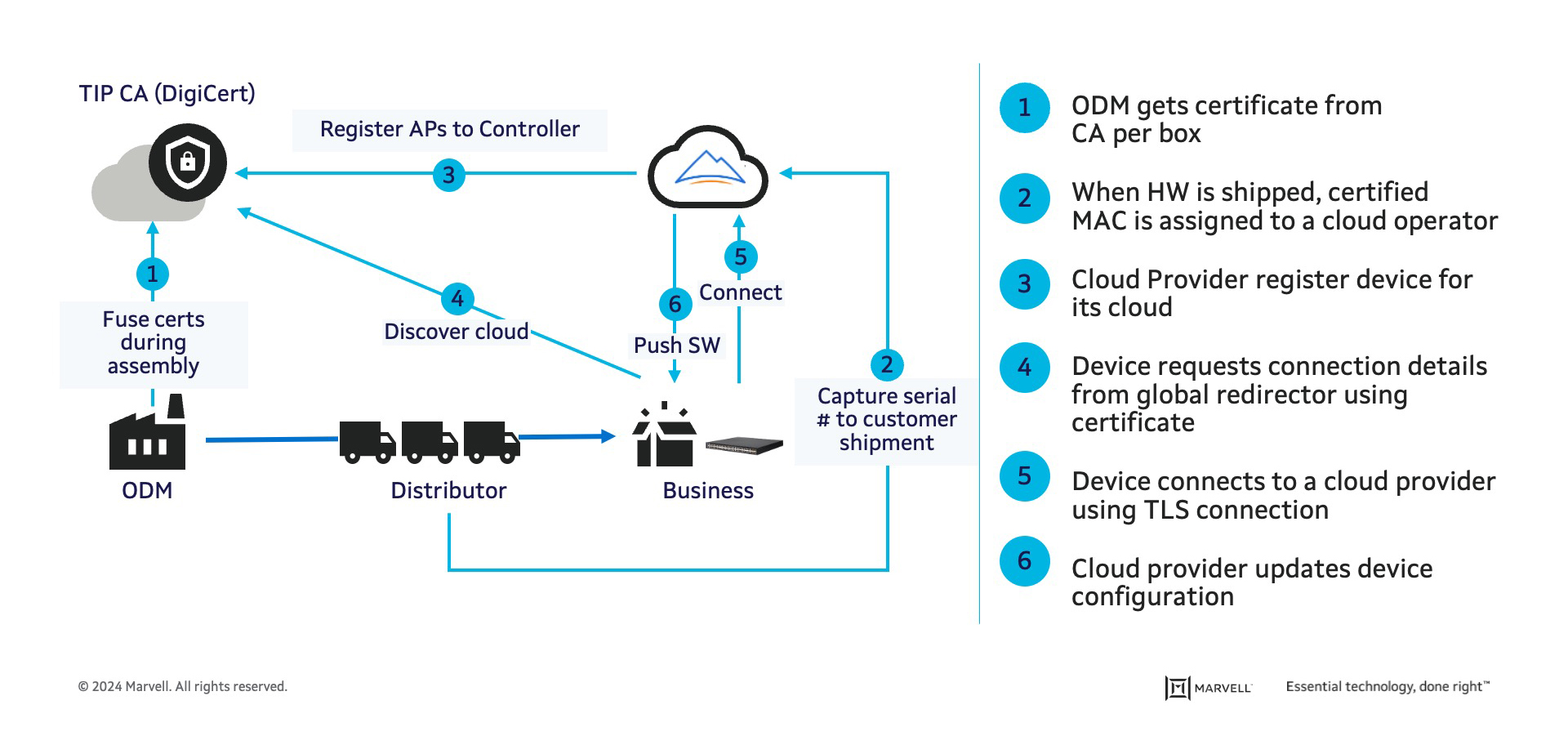
Figure 5: Zero Trust Provisioning
Summary
Campus networks have eagerly awaited the advantages of open networking, the robust capabilities of SONiC and the operational efficiencies of cloud management. Marvell, along with the entire OpenLAN Switching community, has collaboratively created a solution that perfectly caters to the needs of the Cloud Managed Enterprise (CME) market. The Marvell Prestera switches play a pivotal role in this exciting new market.
This blog contains forward-looking statements within the meaning of the federal securities laws that involve risks and uncertainties. Forward-looking statements include, without limitation, any statement that may predict, forecast, indicate or imply future events or achievements. Actual events or results may differ materially from those contemplated in this article. Forward-looking statements are only predictions and are subject to risks, uncertainties and assumptions that are difficult to predict, including those described in the “Risk Factors” section of our Annual Reports on Form 10-K, Quarterly Reports on Form 10-Q and other documents filed by us from time to time with the SEC. Forward-looking statements speak only as of the date they are made. Readers are cautioned not to put undue reliance on forward-looking statements, and no person assumes any obligation to update or revise any such forward-looking statements, whether as a result of new information, future events or otherwise.