- PRODUCTS
- COMPANY
- SUPPORT
- PRODUCTS
- BY TYPE
- BY MARKET
- COMPANY
Our Company
Media
Contact
- SUPPORT
Cryptomathic and Marvell: Enhancing Crypto Agility for the Cloud
Grab a cup of coffee. In this blog I describe how IT professionals can utilize Marvell® LiquidSecurity® Hardware Security Modules (HSMs) with Cryptomathic’s Crypto Service Gateway.
Cryptomathic has 35+ years of experience providing global secure solutions to a variety of industries, including banking, government, technology manufacturing, cloud, and mobile. The company’s Crypto Service Gateway software is a first-of-its-kind central cryptographic platform that provides centralized and crypto-agile management of third party HSM hardware, enhancing the behavior of HSMs while improving the time-to-market of business applications.
An HSM is a physically secure computing device that safeguards and manages digital keys, performs encryption/decryption functions, and provides strong authentication mechanisms. They typically come in two form factors: a PCIe card or a 1U network attached server. They are NIST (National Institute of Standards and Technology) FIPS 140-3, level-3 certified and most provide tamper evidence (visible signs of tampering), tamper resistance (the HSM becomes inoperable upon tampering) or tamper responsive (deletion of keys upon tamper detection). All provide logging and alerting features, strong authentication, and key management features, and support common APIs like PKCS#11. Applications that require cryptographic services will make API calls for keys used to encrypt data in motion or at rest.
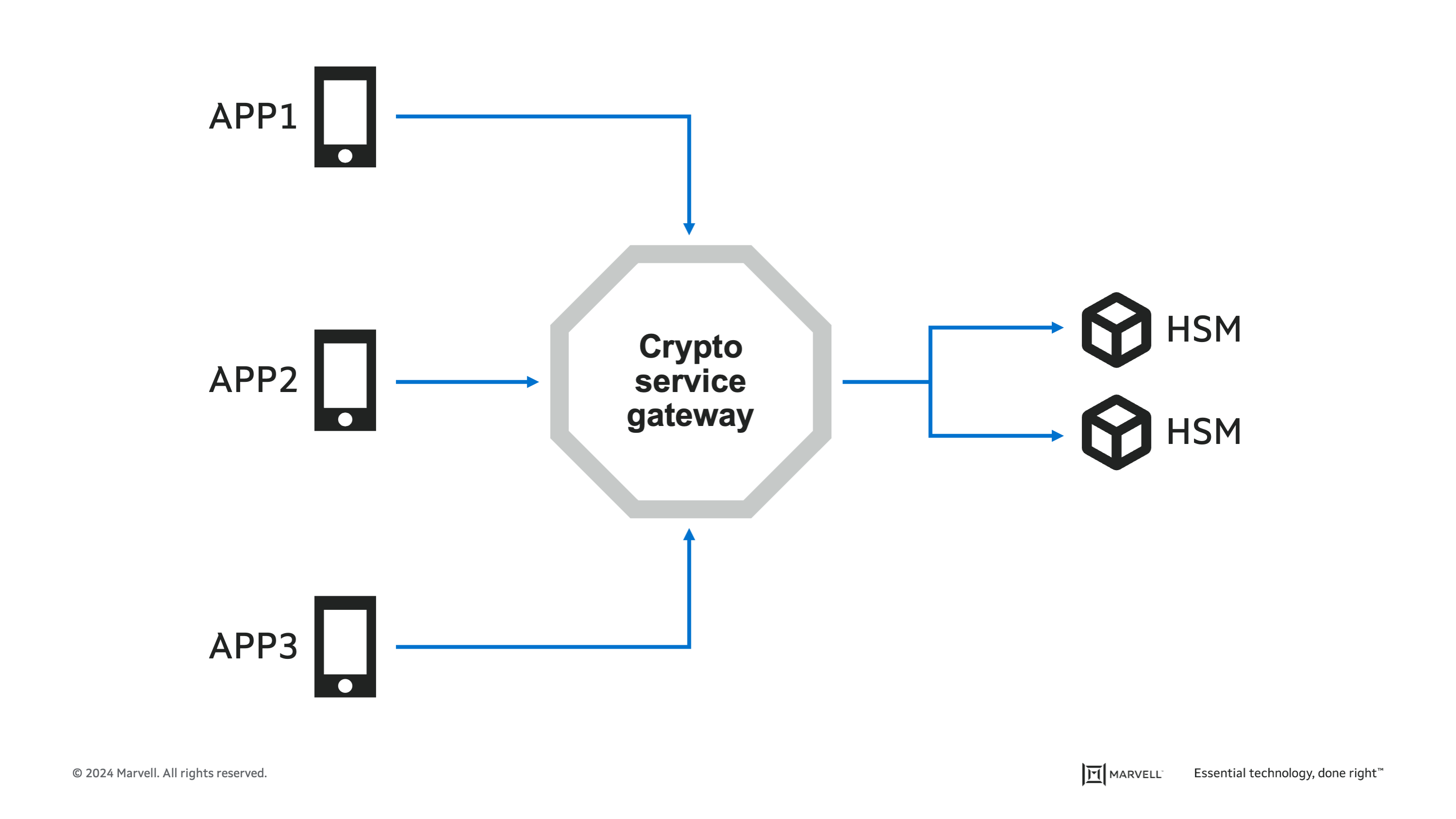
Many large enterprise companies have a mixture of on-premises HSMs from different vendors. Although all the HSMs today support common APIs like PKCS#11, each has a different way of authentication, auditing, and managing keys. Because of this, large enterprises are forced to manage separate key management software from the different vendors. And when these large enterprise customers want to run their applications in a hybrid (on-premises / cloud) environment, it forces them yet again to manage a new key management service in the cloud.
Cryptomathic’s CSG software serves as a “shim” layer that sits between an enterprise’s applications and the third party HSMs and is independent of them. Companies can now manage HSM hardware from any vendor with a single pane of glass key management software solution from Cryptomathic. In addition to vendor-independent, optimized utilization of HSM resources, Cryptomathic’s CSG software delivers centralized policy enforcement for all crypto operations, which keeps crypto decisions in the hands of the security team, simplifies compliance audits and facilitates crypto-agility.
The Marvell LiquidSecurity family of HSMs pioneered the idea of taking HSMs into the cloud. Rather than manage an armada of their own appliances, organizations can subscribe to HSM services from cloud providers or employ a combination of services from different clouds and self-owned systems. LiquidSecurity 2, our latest model, can manage up to 1 million keys and supports 42 partitions for secure multitenancy.
Another critical distinction is that, instead of being a 1U or 21U pizza box, LiquidSecurity HSMs fit into a PCIe slot to reduce cost, power and rack space. (Technology for LiquidSecurity came from Cavium, a processor company specializing in security and networking processors which Marvell acquired in 2018, and in-house Marvell technology for cloud optimization.) Six of the top ten cloud providers use LiquidSecurity devices.
When you look at the capabilities of both technologies, you can likely see why we are working together. Organizations want and need to maintain control over their HSM capabilities, and it’s a challenge that becomes even more difficult when the underlying hardware systems are in different locations and operated by different service providers. By combining the two, organizations can maintain the performance and agility they require through Cryptomathic while taking advantage of the economics and scalability of the cloud.
With our tested integration, companies can utilize Cryptomathic’s CSG software with Marvell LiquidSecurity HSM hardware. The combined solution provides the flexibility required in a hybrid on-premises/cloud environment.
# # #
Marvell and the M logo are trademarks of Marvell or its affiliates. Please visit www.marvell.com for a complete list of Marvell trademarks. Other names and brands may be claimed as the property of others.
This blog contains forward-looking statements within the meaning of the federal securities laws that involve risks and uncertainties. Forward-looking statements include, without limitation, any statement that may predict, forecast, indicate or imply future events or achievements. Actual events or results may differ materially from those contemplated in this blog. Forward-looking statements are only predictions and are subject to risks, uncertainties and assumptions that are difficult to predict, including those described in the “Risk Factors” section of our Annual Reports on Form 10-K, Quarterly Reports on Form 10-Q and other documents filed by us from time to time with the SEC. Forward-looking statements speak only as of the date they are made. Readers are cautioned not to put undue reliance on forward-looking statements, and no person assumes any obligation to update or revise any such forward-looking statements, whether as a result of new information, future events or otherwise.
Tags: Security
Recent Posts
Archives
Categories
- 5G (12)
- AI (30)
- Automotive (26)
- Cloud (16)
- Coherent DSP (10)
- Company News (103)
- Custom Silicon Solutions (7)
- Data Center (55)
- Data Processing Units (22)
- Enterprise (25)
- ESG (6)
- Ethernet Adapters and Controllers (12)
- Ethernet PHYs (4)
- Ethernet Switching (41)
- Fibre Channel (10)
- Marvell Government Solutions (2)
- Networking (36)
- Optical Modules (15)
- Security (6)
- Server Connectivity (26)
- SSD Controllers (6)
- Storage (22)
- Storage Accelerators (2)
- What Makes Marvell (40)
Copyright © 2025 Marvell, All rights reserved.
- Terms of Use
- Privacy Policy
- Contact

